With the rapid increase in technological advancements in recent years, criminals and fraudsters have also become vigilant and clever. Online hackers employ dubious methods to carry out their unethical incentives in harming the credibility of reputable organizations, governments, and individuals, and to gain personal benefits. Due to the currently arising threat of potential cybercrime, online systems need to develop secure and robust frameworks for online safety. With two factor authentication, companies can add an additional layer of security which helps authenticate users using another device for their identity confirmation.
The Omnipresence of Cybercrime
In the past years, companies have lost huge sums of capital as a result of data breaches and cyber-attacks. Traditional security solutions are outwitted and easily deceived by pesky scammers who employ modern impersonation techniques to easily bypass the protection layers. This not only injures the organization’s reputation but also puts the data of its user’s at stake. Information stolen over the internet includes credit card pins, bank account credentials, and social security, and mobile SIM numbers. Any business operating online is prone to these types of attacks including startups, non-profits, small businesses, and global companies.
The effect of cyberattacks is even severe for customers and consumers as their identities are at the risk of being compromised. A study conducted in 2016 unveiled that identity thieves took almost $16 billion from 15.4 million U.S. consumers and the amount lost in identity theft over the past six years came out to be more than $107 billion.
Passwords and 2 Factor Authentication
The historical method of protection used worldwide is good old passwords. Passwords are not the best source of safeguarding user accounts and corporate information anymore. In 1961, the Massachusetts Institute of Technology (MIT) developed a distributed system for students to share resources, but later some eager individuals figured how to hack the system and print out all the passwords.
This was one of those incidents which prove that the regular username and passwords logins are not the ultimate sources of comprehensive security. lousy human memory, a large number of fake accounts, and security fatigue add flame to fire when working with conventional passwords.
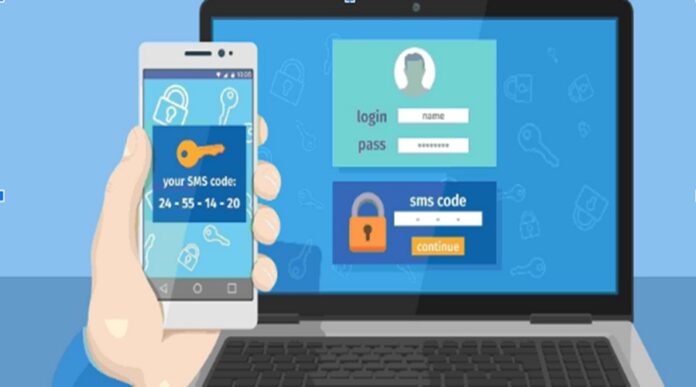
Two-factor authentication, better known as 2-factor authentication or 2FA provides a safer means of user authentication by adding an extra security layer. When 2FA is activated against a user account, they do not readily get access to services as soon as they enter the username and password. Rather, a security code is sent to their email or mobile device, which prompts them to enter the code on the verifying device to authorize them.
This is just one way of performing two-factor authentication. Other methods could require something that the user knows, like a secret question related to their personal identities that are commonly known as Knowledge-Based Authentication (KBA), or they could be asked to verify their fingerprint patterns or perform face recognition for enhanced identification.
Categories of Two-factor Authentication
There are many ways through which 2FA could be achieved. A few methods of achieving the added layer of authentication are below:
SMS-based text messages
As intuitive as it sounds, two-factor authentication performed using SMS sends a security code via. a text message, also known as a One Time Password (OTP) on the user’s mobile device. The user memorizes or writes down the code on a piece of paper and returns back to the application to enter the passcode to gain access. SMS-based 2-factor authentication is considered the least secure means when compared to other methods
Voiced Call Recordings
Unlike passcodes received by text messages in the SMS-based 2FA, a voice-based backend recording is played on a call that informs the users about the password to enter for authentication. Voice-based 2-factor authentication may not be preferred over other 2FA’s when verifying sensitive information like bank credentials or credit card details.
Biometric 2 Factor Authentication
Biometric two-factor authentication incorporates either fingerprint patterns or facial features to validate authorized user identities. Online biometric 2-factor authentication employs face verification and fingerprint scanning to perform secure customer onboarding and prevent online identity theft.